
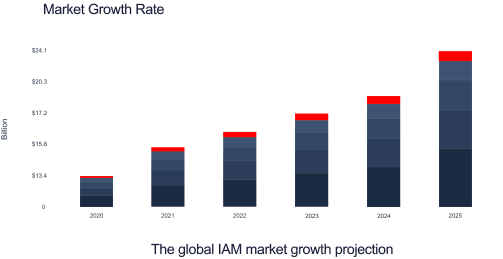
In today's digital landscape, the importance of Identity and Access Management (IAM) in safeguarding data privacy and ensuring regulatory compliance cannot be overstated. With over 22 billion records exposed due to 4000 data breaches in 2023* alone, the importance of Identity and Access Management (IAM) has never been more apparent. Moreover, the average cost of a data breach reached $4.45 million in 2023,** highlighting the financial implications of inadequate IAM practices.
As organizations strive to comply with stringent regulations, the demand for IAM professionals is skyrocketing, with job postings increasing by 28% annually and an estimated 3.5 million unfilled cybersecurity positions by 2025.# IAM expertise is essential across various industries, from finance and healthcare to government and technology, each facing unique challenges in protecting sensitive data and ensuring regulatory compliance.
This course addresses the increasing need for robust IAM frameworks in various business contexts, such as Business-to-Employee (B2E), Business-to-Business (B2B), Business-to-Customer (B2C), and Government-to-Citizen (G2C).
By the end of this course, participants will have developed practical skills to design, implement, and manage IAM systems effectively. They will be equipped to handle IAM processes, ensure compliance, and enhance security across various organizational structures, preparing them for advanced roles in IAM governance and implementation.

Comprehensive digital material for an in-depth understanding of each topic.

Expert-led videos that thoroughly cover all the concepts.

Quizzes after each module to measure and reinforce your knowledge.

Real-world exercises to apply and practice your skills.

A real-world project to demonstrate your expertise.

Proctored exam to validate your skills and proficiency.

From EC-Council University Center of Professional Education.
In this section, we will learn foundational concepts of Identity Access Management (IAM), emphasizing its role in securing access to enterprise assets and ensuring compliance with regulatory standards.
In this section, we will explore the governance aspect of IAM, covering policies, risk management, and fostering a security-aware culture within organizations.
In this section, we will delve into key IAM concepts such as identification, authentication, and authorization, along with various access control models and methods to manage access rights effectively.
In this section, we will examine the organizational processes involved in IAM, including identity lifecycle management, provisioning, incident management, and best practices for managing changes and access reviews.
In this section, we will cover the standards and guidance frameworks relevant to IAM, addressing regulatory compliance, data privacy, and common issues like privilege escalation, while also exploring future trends in the field.
In this section, we will explore Single Sign-On (SSO) and federation in IAM, discussing benefits, challenges, and implementation strategies to provide seamless and secure access across multiple systems.
In this section, we will discuss IAM in the context of cloud computing, covering principles, service models, compliance challenges, and best practices for implementing and managing IAM in cloud environments.
In this section, we will provide a detailed approach to implementing IAM within organizations, covering strategic planning, stakeholder management, project management aspects, and technical integration.
In this section, we will explore various IAM technologies, including architectures, implementations, and supporting tools, to understand their role and practical applications in different environments.
In this section, we will examine emerging trends in IAM such as behavior analytics, artificial intelligence, and blockchain, discussing their implications for security, efficiency, and user experience.
In this section, we will present a case study on establishing identity systems at a national level, covering requirements, solution architecture, challenges, and best practices for managing large-scale identity systems.
In this section, we will present a case study on federated identity management for digital services, discussing requirements, solution architecture, implementation, benefits, and challenges.
In this section, we will present a case study on integrating enterprise IAM systems, focusing on requirements, solution architecture, implementation, and challenges of integrating Active Directory with Azure.
In this section, we will present a case study on implementing Single Sign-On (SSO) for web services using Ping Identity, covering requirements, solution architecture, implementation, and benefits for user authentication and access management.

This certificate course includes hands-on labs to help you gain the practical experience you need. Here is what you will learn by doing.
In today's complex and evolving digital landscape, organizations must effectively manage identities and access to protect sensitive information and ensure secure operations. This lab covers the comprehensive management of Identity and Access Management (IAM) using both Azure Active Directory (Azure AD) and AWS Identity and Access Management (AWS IAM) services. You will also explore the implementation of industry-standard protocols such as OpenID Connect and OAuth2, essential for modern application security.





Showcase your skills with a Certificate of Achievement from EC-Council University
Center of Professional Education. Earn by completing this course.

All the course deliveries are made by EC-Council Certified Instructors. Our live training ensures you receive immediate feedback and guidance, making your learning journey efficient and effective. Whether you're looking to advance your career, gain new skills, or earn a certification, our expert-led courses provide the support and knowledge you need to succeed.
Note: *Pricing for delivery of this course may vary depending on each training partner. These trainings are subject to availability, instructor schedules, and various other factors.
