- About Us
-
- Online Degrees
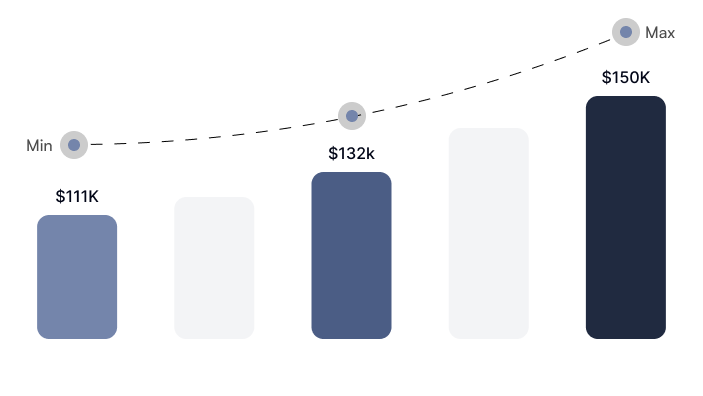
- Master of Science in Cyber Security
- Master of Science in Computer Science
- Masters of Business Administration
- Bachelor of Science in Cyber Security
- Graduate Certificate Program
- Grading System
- Non-Degree
- Managing Secure Network Systems
- Ethical Hacking and Countermeasures
- Investigating Network Intrusions and Computer Forensics
- Security Analysis and Vulnerability Assessment
- Conducting Penetration and Security Tests
- Secure Programming
- Disaster Recovery
- Incident Handling and Response
- Executive Governance & Management
- Designing and Implementing Cloud Security
- Managing Risk in Information Systems
- Auditing IT Infrastructures for Compliance
- iLabs
- Center Of Professional Education
- Why Online
- Services
-
-
Information
-
Benefits
-
Forms
-
-
- Financial Assistance
- Veterans
- Updates